Study Notes - VPC - Inter-Region VPC Peering
來自 AWS News 的訊息,Inter-Region VPC Peering 多了九個 Region,而且總算有亞洲了!不用再自己幹 Site to Site VPN 了!
整理基本資訊、實測的數據、規劃上的考量等。
基本資訊
這次新增支援 Inter-Region VPC Peering 的 Regions 清單如下:
- EU: London, Ireland, Paris
- Asia Pacific: Mumbai, Sydney, Singapore, Tokyo
- Canada: Central
- South America: São Paulo
上次 先 Enable 的 Regions 清單:
- US East: Northern Virgina, Ohio
- US West: Northern California, Oregon
看來全球主要的 region 都已經支援,是相當有誠意的!
這部分,總算可以跟 GCP 的 VPC Network 直接對打了!更多請參考 Compare GCP VPC Network with AWS, Study Notes - VPC Network in GCP
依照官方文件的描述,Inter-Region VPC Peering 會走 AWS 自己的 Backbone,包含擴展、容錯、高可用性 … 都包含了。擷取 官方描述 如下:
Built on the same horizontally scaled, redundant, and highly available technology that powers VPC today, Inter-Region VPC Peering encrypts inter-region traffic with no single point of failure or bandwidth bottleneck.
有了這功能,規劃 Multiple VPC cross Multiple Regions 時,可以有更多的彈性與考量!應該也不用搞 Transit VPC 這麼複雜的東西了吧?!
建立 VPC Peering Connections
如果要使用 awscli 建立,建議先升級版本,我實驗的版本:1.14.4
升級 awscli:
sudo pip install --upgrade awscli
以下為環境變數,REQUESTER 送出 peering 的 region,ACCEPTER 是接受 peering 的 region。
這裡使用 us-east-1 到 ap-northeast-1 當例子。
1 | # Requester: N. Virginia (us-east-1) |
建立 Peering Connection Requester
建立 peering connection 請求,記得指定 --region ,確保送出的 region 是正確的。
1 | aws ec2 create-vpc-peering-connection \ |
如果是跨 AWS Account,則需要另外用 --peer-owner-id 指定 Requester Account ID:
建立成功後,回傳的結果,裡面最重要的就是 VpcPeeringConnectionId
1 | { |
如果是透過 AWS Console 操作,結果如下圖:
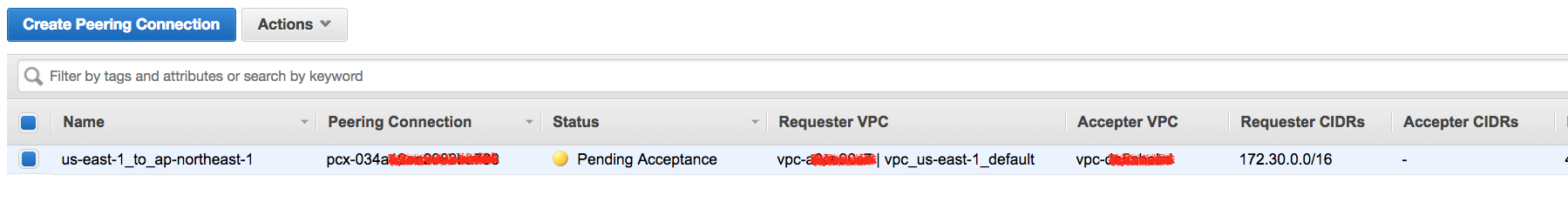
接受 Peering Connection Requester
1 | aws ec2 accept-vpc-peering-connection \ |
1 | { |
如果是透過 AWS Console 操作,結果如下圖:
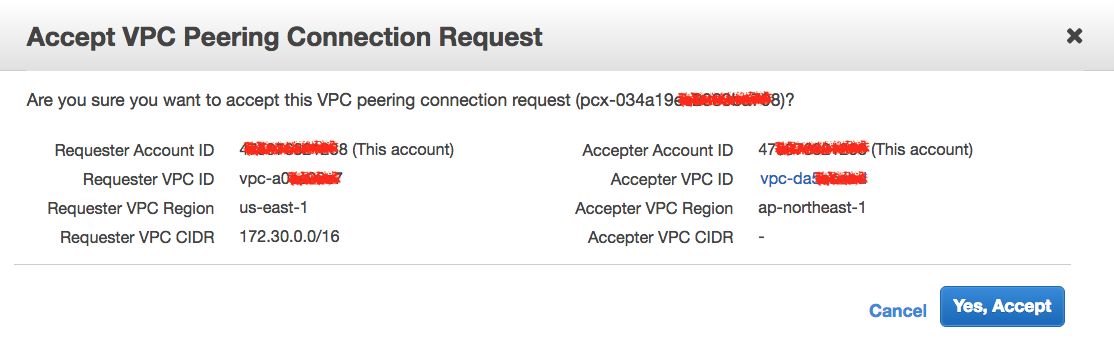
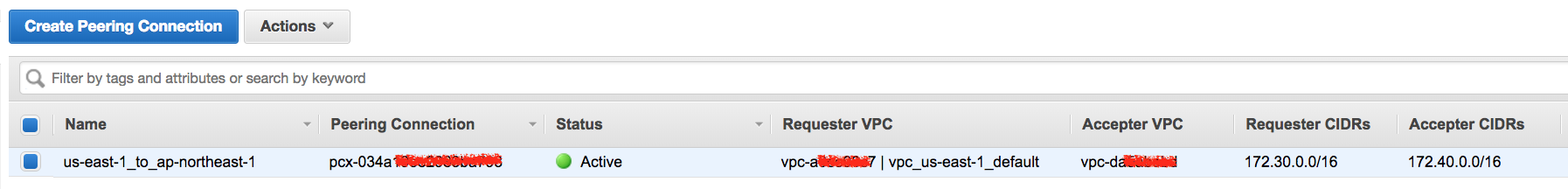
最後的確認結果:
AWS CLI Reference
相關的 AWS CLI
- aws . ec2 . create-vpc-peering-connection
- aws . ec2 . accept-vpc-peering-connection
- aws . ec2 . delete-vpc-peering-connection
調整 Route Table
兩邊的 Route Table 都要加入彼此 CIDR 的範圍,Target 則指定 Peering ID: pcx-12345678912345678
這邊的範例:
- ap-northeast-1: 加入 us-east-1 VPC CIDR 172.30.0.0/16
- us-east-1: 加入 ap-northeast-1 VPC CIDR 172.40.0.0/16
調整 Security Groups
我的 VPC 是依照 Plan and Design Multiple VPCs in Different Regions 提到的規劃,所以新增 VPC 的時候, Private-Default-EC2 就要新增其他 VPC CIDR ,允許彼此可以互通。
這邊的範例:
Private-Default-EC2in ap-northeast-1: 加入 us-east-1 VPC CIDR 172.30.0.0/16Private-Default-EC2in us-east-1: 加入 ap-northeast-1 VPC CIDR 172.40.0.0/16
這些調整每個公司會有不同的資安政策,上述只是我的方法而已。
調整 Network ACLs
如果 VPC 規劃也有控管 Network ACLs,同樣的,也要針對不同的 VPC 來源作配置。
測試傳輸速度
使用兩個方法測試:
- iperf3 直接對測
- 傳檔案: 10MB, 100MB, 1000MB
先在兩邊 EC2 Instance 準備以下資料:
1 | ## Install iperf3 |
因為我本來就有開一台 t2.micro,所以弄了另外一組,測了以下兩個組合:
- 東京 (c4.xlarge) <—> 美東 t2.micro
- 東京 (c4.xlarge) <—> 美東 c5.large
因為東京還沒有 c5 可以測,所以預期上限會在 c4.xlarge.
t2.micro (us-east-1) to c4.xlarge (ap-northeast-1)
東京:c4.xlarge, Network High
美東:t2.micro, Network Low
實測:
1 | root@ip-172-30-3-94:~# iperf3 -c 172.40.0.73 |
傳檔案:us-east-1 to ap-northeast-1
1 | scp -i gtcafe-dev.japan.lab.pem 10M.dummy ec2-user@172.40.0.73:/tmp |
小結: 整體速度上限在
6.5MB/s的速度
c5.large (us-east-1) to c4.xlarge (ap-northeast-1)
東京:c4.xlarge, Network High
美東:c5.large, Network Up to 10 Gigabit
1 | [ec2-user@ip-172-30-3-42 ~]$ iperf3 -c 172.40.0.73 |
傳檔案: us-east-1 to ap-northeast-1
1 | scp -i gtcafe-dev.japan.lab.pem 10M.dummy ec2-user@172.40.0.73:/tmp |
小結: 整體速度上限在
11.5MB/s的速度
結論
整體的速度大概會跟 Inter-Region VPC Peering 的限制有關係,所以實測上的數字,很難超過 EC2 本身提供的 Network Performance.
規劃的考量
- 調整 Route Table, Security Groups, Network ACLs 的配置
- 未來管控的 Policy 要重新 Review
- Review VPC 的 Topology
- 實測 Throughput,是否能夠滿足特定應用的需求,像是 Database Replication
- 確認有資料加密
- 成本:
- 連接的成本:No
- 資料傳輸的成本:標準跨區域資料傳輸費用計算 – 沒有寫得很清楚,待查
- CIDR Planning: CIDR 空間不能 overlap
延伸閱讀
系列文章
- Study Notes - Virtual Private Cloud (VPC)
- Study Notes - VPC - Security Groups and Network ACLs
- Study Notes - VPC Peering and Private DNS using Route53
- Study Notes - VPC - Inter-Region VPC Peering
- Study Notes - VPC FAQ
- Plan and Design Multiple VPCs in Different Regions
- From One to Many - Evolving VPC Design
- Migrate to AWS NAT Gateway
- Unknown ENI Delete Action in CloudTrial
- Study Notes - VPC IPv6 Support
相關文章
- Lambda Network Traffic Test in VPC w/ or w/o Endpoint
- 設定 VPC Peering and Private DNS using Route53
- GCP: Compare GCP VPC Network with AWS
- GCP: Study Notes - VPC Network in GCP
相關資料
- Inter-Region VPC Peering is Now Available in Nine Additional AWS Regions - 2018/02/20
- New – Inter-Region VPC Peering - 2018/01/22
- New VPC Peering for the Amazon Virtual Private Cloud - 2014/05/26
- VPC Peering Guide



